 |
 |
Amduus Information Works, Inc.
Copyright 2001 Amduus Information Works, Inc.
Table of Contents
About Amduus Information Works, Inc.
Determining the version of your encryptor:
Configuring the encryption compiler
Limitations of what can be encrypted.
Performing a compile of an encrypted file
Amduus Information Works, Inc. is based in Sunnyvale California, the heart of the Silicon Valley.
The company creates programs for sale, re-sale, and out in the Open Source world. The company can be contracted for the creation, installation, configuration, and modification of applications.
More information can be found at http://www.amduus.com or sales@amduus.com.
There will be times when you need to share source code without wanting to share the code. This is because .r files need to be recompiled from source when those files use a database table that has changed.
This program is a cheap and easy means of accomplishing that. It uses a combination of two somewhat well known encryption methods.
Note that this program keeps honest people honest. The algorithm is based on a block cipher and block ciphers can have cryptanalysis performed on them. But it is safe enough to be a nuisance to people who might want a peek at source code released out into the “wild.”
In general, it works like this:
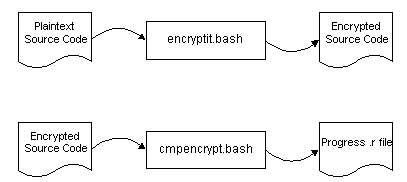
The reason this program was written was to release code into the wilds of the internet, where by some of the program was open source and could be modified by the user, and other parts remain proprietary so that the user would need to contract with Amduus Information Works, Inc. to make changes.
There are different versions of encryptor available. This document is written for version named on the title page. The versions previous to version 1.4 are not backwards compatible, so knowing the version you are working with is important.
Encryptor is written using the RCS[1] source code control system. By entering the following command, you will be able to determine your version number (in bold):
[/appl/encrypt]$ ident encryptit.p
encryptit.p:
$Header: /home/appl/encrypt/RCS/encryptit.p,v 1.4 2001/11/06 18:48:07 sauge Exp sauge $
The distribution file is a zip file named dist3.zip. This file should be downloaded from the Open Source area of Amduus Information Works, Inc. at http://www.amduus.com.
Follow these steps:
Compiling an encrypted program produces a .r file which is in sync with the definition of the database tables it uses. In order for the creation of the .r file, the compile program needs to have access to the database the compiled source is to run against.
Note: You cannot run this program on a query/run time license – you must have Provision or the 4GL Development system installed and in use. You CAN run the resulting .r on a run-time version of the progress client however.
This is done in the normal Progress fashion by using the –pf argument on the
command line invocation of the progress executable.
# Compile an encrypted program
if [ -z "$1" ]; then
echo "(c) 2001 Amduus Information Works, Inc. http://www.amduus.com"
echo cmpencrypt.bash [filename] [passphrase]
exit 0
fi
export FILENAME=$1
export PASSPHRASE=$2
$DLC/bin/_progres -b -p cmpencrypt.p –pf Your_PF_File
# $Header: /home/appl/encrypt/RCS/cmpencrypt.bash,v 1.2 2001/11/06 00:22:21 sauge Exp sauge $
It is assumed the Progress oriented variables are already available in the shell invoking the command.
Only .p and .w files can be compiled. It is based on the limitations of the COMPILE statement – hence, include files cannot be compiled in encrypted form. Hopefully this limitation will be eliminated in the next version.
The encryption command does not encrypt the original source file. It creates an encrypted copy in a different directory. You should never encrypt the same file in the same directory. There is no convenient way back.
Typing the command without any arguments will provide an argument list for easy reference of how the command should be invoked.
[/appl/encrypt]$ encryptit.bash
(c) 2001 Amduus Information Works, Inc. http://www.amduus.com
encryptit.bash [filename] [output_directory] [passphrase]
An example invocation:
[/appl/encrypt]$ encryptit.bash cmpencrypt.p dist gfdthe4563d
This call takes the cmpencrypt.p file in the current working directory, encrypts it with the pass phrase gfdthe4563d and places an encrypted copy in the dist sub-directory. Absolute directory paths, etc. can be used safely.
Note: The encryption program does not compile against any databases, so it does not need a database connection. The .r that comes with the package is for Version 9 of Progress and should work on query run-time licenses.
Before compiling any encrypted files that manipulate database tables, be sure to have the encryption script configured to speak with the database server.
Typing the command without any arguments will provide an argument list for easy reference of how the command should be invoked.
[/appl/encrypt]$ cmpencrypt.bash
(c) 2001 Amduus Information Works, Inc. http://www.amduus.com
cmpencrypt.bash [filename] [passphrase]
An example invocation:
[/appl/encrypt]$ cmpencrypt.bash dist/cmpencrypt.p gfdthe4563d
This example invocation compiles the file dist/cmpencrypt.p with the pass phrase of gfdthe4563d. The resulting .r file will be placed in the same directory as the encrypted source file.
In order to compile an encrypted program, you must have the pass phrase used to encrypt the program.
Text that has undergone encryption by a cryptosystem. Cipher text should be secure from view to the world.
Science and Art of code breaking
Practitioner of Cryptanalysis
Mathematical function for encryption and decryption.
The process of converting cipher text into plain text.
The process of converting plain text into cipher text.
Text that has not been encrypted yet, or has been decrypted from cipher text. Plain text is viewable to the world.
Bruce Schneier, Applied Cryptography 2nd Edition, ISBN 0-471-12845-7
Neal Koblitz, Algebraic Aspects of Cryptography, ISBN 3-540-63446-0
Wayne Patterson, Mathematical Cryptology, ISBN 0-8476-7438-X
[1] CVS is based on RCS tags, so it should work also.